When the police’s IT-systems are not in order, everyone loses
Without the trust of citizens, the police cannot do their job properly. That is why it is important that the police are extremely careful with citizens' data. But an analysis by EDRi member Bits of Freedom shows that of all 36 'mission critical' systems of the police, not one complies with the rules on privacy and information security.
Mission critical
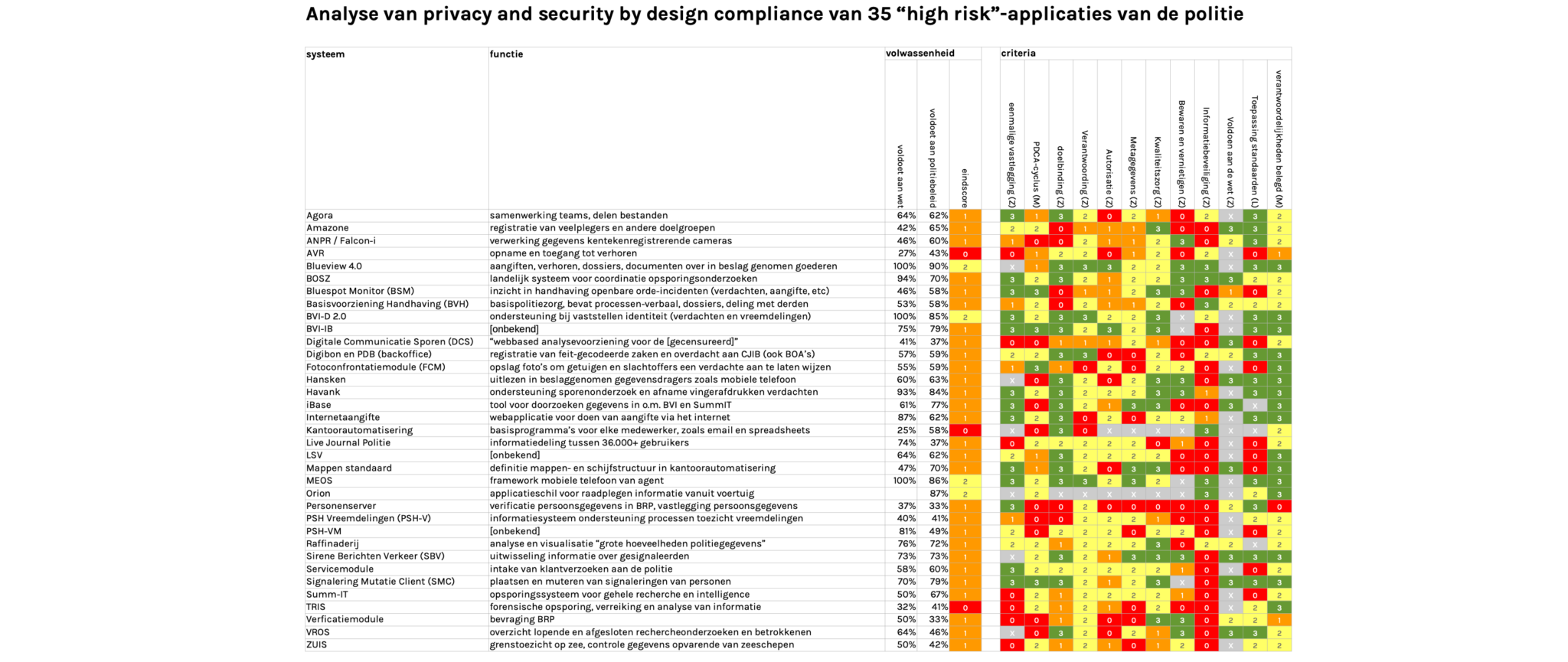
This analysis concerns 36 systems, which, according to the police, “must remain operational at all times, so that the police can do their job”. They are the systems for registering repeat offenders and license plates, taking statements and interrogations, exchanging information between police officers, processing fingerprints, analysing big amounts of sensitive data and many other functions. None (!) of these systems comply with the rules on privacy and security by design that follow from the law and police policies.
The table below is a summary of our analysis: everything, except the gray fields, are supposed to be green.
Designed by: Foto: Photoholgic
The nation’s best-known law enforcement agency has a long history of law violations
It is about time that the regulatory body does what the police themselves do: hand out fines
Expectations for the near future are no better. In a status update the police note “a negative outcome” and that “even scores have gone down”. According to the police, “a realistic expectation is that 50% of our applications complying will meet legal requirements by the end of 2020”. As far as we are concerned, past experiences give no reason to be so optimistic. But more importantly: that also means that half of the applications still do not meet the legal requirements.
A witness to a liquidation will not tell their story to the police if that puts them in extra danger.
Secondly, it is important that the minister not only looks the law itself in the planned amendment of the law, but also at its feasibility. The police previously stated that data that must be removed is not removed because the computer systems are too old. If you want to create a new law that functions properly, you might also have to invest in police IT-systems.
(Contribution by Rejo Zenger Beleidsadviseur)
This is a translation of a Dutch article. A big thank you to two translators: Alex Leering and Martin van Veen.
The article was first published by Bits of Freedom.

